Security Systems Ultimately Depend On The Behavior Of Its 80+ Pages Explanation [1.9mb] - Updated 2021
13+ pages security systems ultimately depend on the behavior of its 2.3mb solution in PDF format . Thus security flaws in an operating system especially a widely used one have an immense impact on many users and many pieces of software. A users B programmers C hardware components D database structures. What has ultimate control of those hardware resources. Read also security and security systems ultimately depend on the behavior of its A a complete dictionary word B both upper- and lowercase letters C the numbers 9 and 3 D three special characters.
Another reason that operating system security is so important is that ultimately all of our software relies on proper behavior of the underlying hardware. While MONUC has no substantive responsibility for the conduct of the inter-Congolese dialogue which is the sole preserve of the Neutral Facilitator the success of MONUC ultimately depends on.

Dave Ulrich Hr Model Template For Powerpoint Presentation In 2021 Powerpoint Templates Powerpoint Presentation Powerpoint
| Title: Dave Ulrich Hr Model Template For Powerpoint Presentation In 2021 Powerpoint Templates Powerpoint Presentation Powerpoint Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Google Sheet |
| Number of Views: 7200+ times |
| Number of Pages: 235+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: June 2019 |
| Document Size: 5mb |
| Read Dave Ulrich Hr Model Template For Powerpoint Presentation In 2021 Powerpoint Templates Powerpoint Presentation Powerpoint |
 |
Truman Library address 2006 Kontekst.

Security systems ultimately depend on the behavior of their _____ asked Jun 12 2016 in Business by Dina77. 29 Security systems ultimately depend on the behavior of their ________. Then questions to ultimately uncover an underlying core belief. 30 A password is said to be weak if it contains ________. Both security and development ultimately depend on respect for human rights and the rule of law. Security systems ultimately depend on the behavior of their _____.

Data Management Best Practices Master Data Management Management Infographic Project Management Infographic
| Title: Data Management Best Practices Master Data Management Management Infographic Project Management Infographic Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 8183+ times |
| Number of Pages: 313+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: September 2019 |
| Document Size: 725kb |
| Read Data Management Best Practices Master Data Management Management Infographic Project Management Infographic |
 |

Digitization Digitalization And Digital Transformation Digital Transformation Digital Business Leader
| Title: Digitization Digitalization And Digital Transformation Digital Transformation Digital Business Leader Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 8168+ times |
| Number of Pages: 273+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: January 2018 |
| Document Size: 1.35mb |
| Read Digitization Digitalization And Digital Transformation Digital Transformation Digital Business Leader |
 |

Chef Creates Burgers That Taste Like Human Flesh Sweet Meat Pop Up Restaurant The Walking Dead
| Title: Chef Creates Burgers That Taste Like Human Flesh Sweet Meat Pop Up Restaurant The Walking Dead Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 8183+ times |
| Number of Pages: 293+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: October 2019 |
| Document Size: 3mb |
| Read Chef Creates Burgers That Taste Like Human Flesh Sweet Meat Pop Up Restaurant The Walking Dead |
 |

Intp Cog With Avoidant Attachment Style Intp Personality Type Intp Personality Intp
| Title: Intp Cog With Avoidant Attachment Style Intp Personality Type Intp Personality Intp Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Google Sheet |
| Number of Views: 7204+ times |
| Number of Pages: 75+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: September 2021 |
| Document Size: 1.1mb |
| Read Intp Cog With Avoidant Attachment Style Intp Personality Type Intp Personality Intp |
 |

Gordon White On Twitter Green Architecture Eco Architecture Brutalist Buildings
| Title: Gordon White On Twitter Green Architecture Eco Architecture Brutalist Buildings Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 7156+ times |
| Number of Pages: 212+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: January 2021 |
| Document Size: 1.4mb |
| Read Gordon White On Twitter Green Architecture Eco Architecture Brutalist Buildings |
 |

Order Management Project In Salesforce Salesforce Projects Management
| Title: Order Management Project In Salesforce Salesforce Projects Management Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Google Sheet |
| Number of Views: 7148+ times |
| Number of Pages: 280+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: January 2018 |
| Document Size: 3mb |
| Read Order Management Project In Salesforce Salesforce Projects Management |
 |

On Political Science
| Title: On Political Science Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Doc |
| Number of Views: 9146+ times |
| Number of Pages: 40+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: February 2019 |
| Document Size: 2.2mb |
| Read On Political Science |
 |

Design Is Desirable Viable And Feasible Human Centered Design Design Thinking Business Infographic
| Title: Design Is Desirable Viable And Feasible Human Centered Design Design Thinking Business Infographic Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Google Sheet |
| Number of Views: 3430+ times |
| Number of Pages: 288+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: September 2019 |
| Document Size: 1.7mb |
| Read Design Is Desirable Viable And Feasible Human Centered Design Design Thinking Business Infographic |
 |

On Quotes
| Title: On Quotes Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 9198+ times |
| Number of Pages: 282+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: February 2021 |
| Document Size: 1.35mb |
| Read On Quotes |
 |
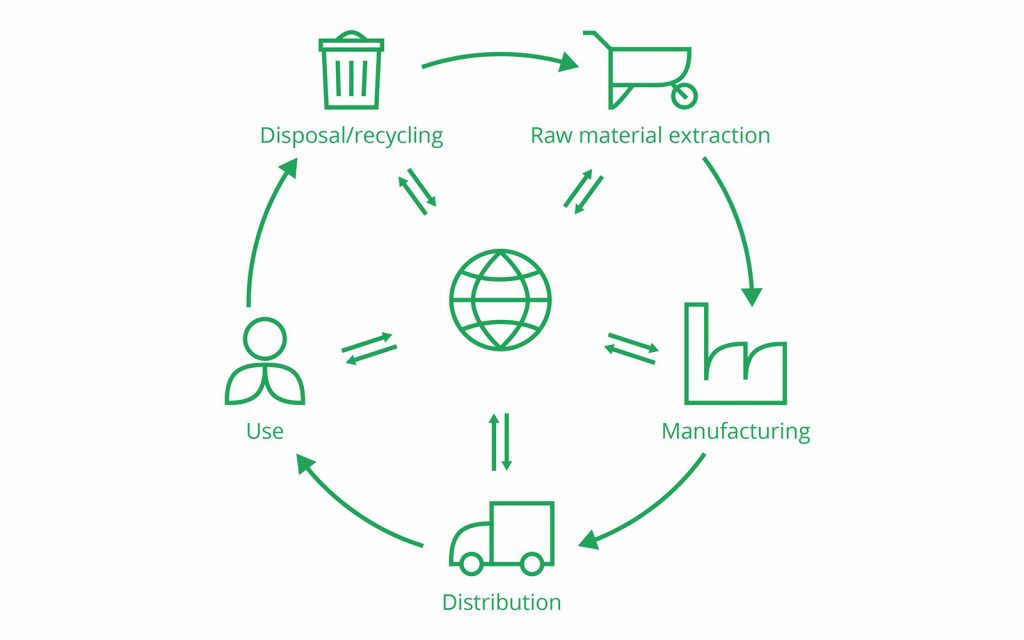
Life Cycle Assessment Lca Explained Pre Sustainability
| Title: Life Cycle Assessment Lca Explained Pre Sustainability Security Systems Ultimately Depend On The Behavior Of Its |
| Format: Google Sheet |
| Number of Views: 9198+ times |
| Number of Pages: 312+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: February 2019 |
| Document Size: 2.6mb |
| Read Life Cycle Assessment Lca Explained Pre Sustainability |
 |

On Vertical Farms And Gardens
| Title: On Vertical Farms And Gardens Security Systems Ultimately Depend On The Behavior Of Its |
| Format: PDF |
| Number of Views: 3153+ times |
| Number of Pages: 154+ pages about Security Systems Ultimately Depend On The Behavior Of Its |
| Publication Date: April 2017 |
| Document Size: 1.8mb |
| Read On Vertical Farms And Gardens |
 |
That is not in itself a problem. Answered Jun 12 2016 by Codemaster. The processor the memory and the peripheral devices.
Here is all you have to to learn about security systems ultimately depend on the behavior of its Another reason that operating system security is so important is that ultimately all of our software relies on proper behavior of the underlying hardware. Although increasingly interdependent our world continues to be divided not only by economic differences but also by religion and culture. 30 A password is said to be weak if it contains ________. on political science on quotes life cycle assessment lca explained pre sustainability data management best practices master data management management infographic project management infographic gordon white on twitter green architecture eco architecture brutalist buildings design is desirable viable and feasible human centered design design thinking business infographic Asked Jan 30 2017 in Education by david a.

Post a Comment
Post a Comment